Two days ago, SandboxEscaper released another PoC exploit for a Windows 10 Task Scheduler local privilege escalation flaw, leading to privilege escalation and allowing users to gain full control over files that would otherwise only be accessible to privileged users like SYSTEM and TrustedInstaller. Yesterday, SandboxEscaper dropped two more vulnerability-related PoC exploits— a sandbox escape flaw in Internet Explorer 11 (zero-day) and a Windows Error Reporting (previously patched) local privilege escalation vulnerability. The reason behind these vulnerability releases is a May 22 post from the blog of SandboxEscaper. Today, another post says the two remaining bugs were: The remaining bugs have been uploaded. I like bridges burning. I hate this world alone. Ps: this month apparently patched the last Windows error reporting bug. Other 4 bugs are still 0days on the GitHub. Have fun, have fun.
Escalation of local privileges PoC
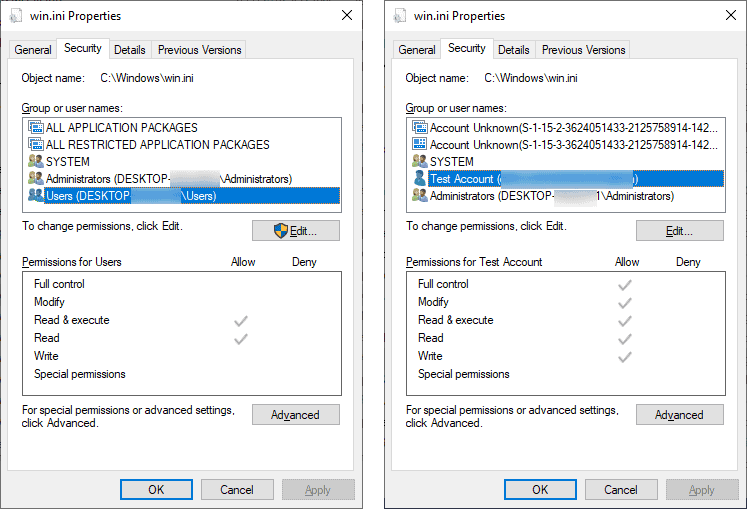
SanboxEscaper found the zero-day Local Privilege Escalation flaw dubbed CVE-2019-0841-BYPASS after noticing that “vulnerability is still present in code triggered by CVE-2019-0841.” The CVE-2019-0841 is a “Windows Privilege Vulnerability Elevation” which was patched in the May 2019 patch Tuesday updates. “An elevation of privilege vulnerability exists when Windows AppX Deployment Service (AppXSVC) improperly handles hard links. An attacker who successfully exploited this vulnerability could run processes in an elevated context. An attacker could then install programs; view, change or delete data.” According to the researcher, this new vulnerability bypasses the patch for Microsoft’s CVE-2019-0841, enabling attackers to write a DACL that will “identify trustees that are allowed or denied access to a secure object” after successful exploit. As she describes the process of exploitation: If you create the following: (GetFavDirectory() gets the local appdata folder, fyi) CreateDirectory(GetFavDirectory() + L”\Packages\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe”,NULL); CreateNativeHardlink(GetFavDirectory() + L”\Packages\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe\bear3.txt”, L”C:\Windows\win.ini”); If we create that directory and put an hardlink in it, it will write the DACL. !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!IMPORTANT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe this part has to reflect the currently installed edge version. You can find this by opening edge -> settings and scrolling down. !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!IMPORTANT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! SandboxEscaper delivers PoC executables in the PoCFiles repository of CVE-2019-0841-BYPASS that can be used to test vulnerability on patched Windows machines.
Hard to reproduce LPE PoC
The other zero-day PoC feature released today by the researcher and dubbed InstallerBypass is also for local privilege increases and can be used to deploy binaries to the Windows folder of system32 and to run them with enhanced privileges. As SandboxEscaper says “Could be used with a malware, you can programmably trigger the rollback. Maybe you can even pass the silent flag to hide your installer user IT and find a new way to trigger a rollback (e.g. by using the installer api, injecting it into medium msiexec IL etc.).