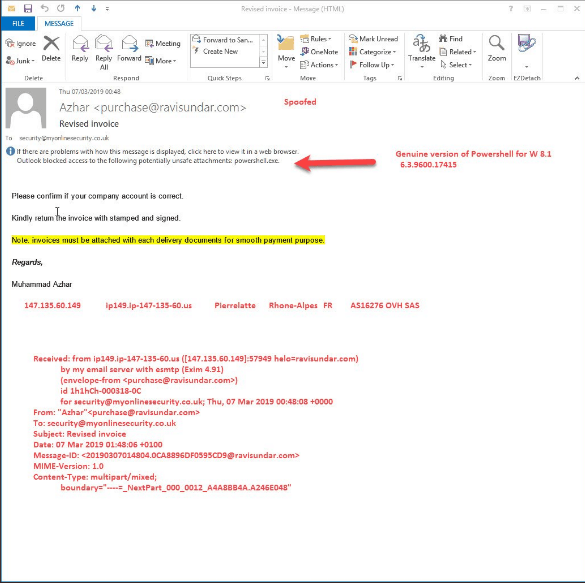
A recently caught phishing email did not deliver some kind of malicious payload to the victim, as one would expect, but the executable of the legitimate PowerShell command line utility found in Windows operating system. The command line tool was the genuine tool available in Windows 8.1 to eliminate all confusion, and it did nothing on the victim’s computer. The phishing message was sent to My Online Security’s inbox and came with a spoofed sender address, pretending to communicate about an invoice, requesting confirmation of the company’s account. It also came with “powershell.exe” in the attachment, which was blocked for security reasons by Outlook, as would all major email services.
— My Online Security (@dvk01uk) March 7, 2019 That’s why unless you rename its extension; you can’t send an executable file over email. Derek from My Online Security believes that the phisher might have wanted to use a shortcut LNK file for the attack, a method that has been used regularly recently to deliver malicious payloads.
Cozy Bear’s spear phishing campaigns (a.k.a. APT29, CozyCar, OfficeMonkeys, The Dukes, CozyDuke, and Grizzly Steppe) first observed turning shortcut files into payloads. Malware analysts found PowerShell commands and scripts to run on the victim machine were included in the shortcut. After an IT engineer named Felix revealed in a blog post how to arm a shortcut file to drop an arbitrary payload, this method has grown in popularity. It was used with a torrent download through The Pirate Bay earlier this year. The shortcut posed as the film file in that case, but its author failed to give it a proper icon to keep suspicions at bay. In pirated content, malicious. LNK is quite common as a warning.