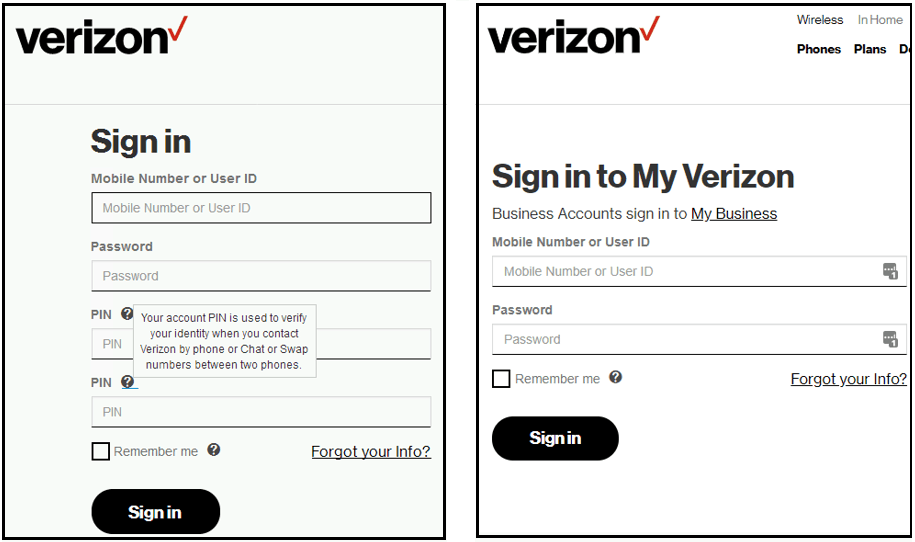
On August 5, Verizon Wireless Users, T-Mobile customers on August 12, and Sprint customers on August 19 were supplemented with new modules. The webinjects enable the threat group behind the TrickBot botnet–dubbed Secureworks GOLD BLACKBURN–to inject further code via internet meetings within their victim’s websites. “When a victim navigates to the website of one of these organizations, the legitimate server response is intercepted by TrickBot and proxied through a command and control (C2) server,” explain the researchers.
TrickBot targeting Verizon users (the altered version on the left, original on the right) The server will then automatically inject HTML and JavaScript into the web browser of the victim, adding the customers of the three mobile providers “an additional form field that requires user’s PIN code.” This version of TrickBot also injects code to capture and exfiltrate the harvested username, password, and PIN on its C2 server, apart from injecting an additional pin request form into the target login pages. The Secureworks scientists discovered that “these’ recordings’ are submitted to TrickBot operators as they browse through infected hosts on their internet panels.” Following mobile user PIN codes indications of the participation or concern amongst actors threatening to operate a SIM swap fraud system (SIM scattering or Port-Out scam) that would allow them to take complete control of their victims ‘ telephone numbers, “including all text and voice communications, both inbound and outbound.”
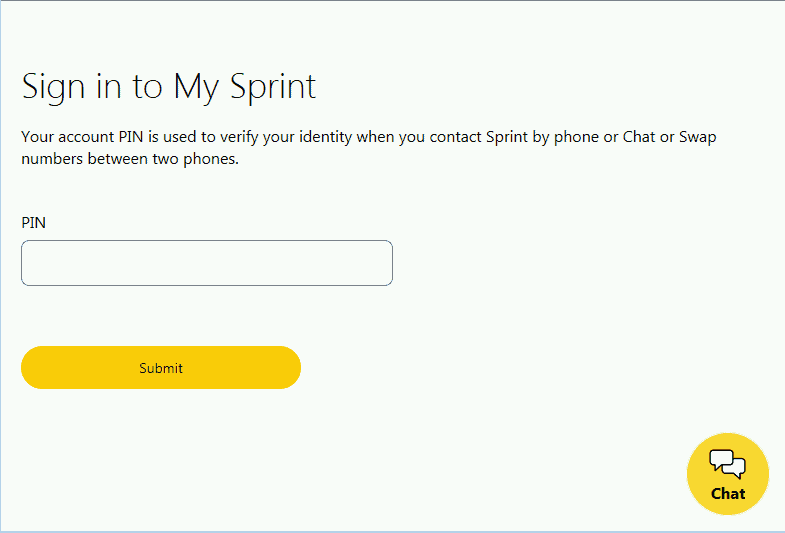
PIN code attack targeting Sprint users “The interception of short message service (SMS)-based authentication tokens or password resets is frequently used during account takeover (ATO) fraud,” adds the report. Organizations and users can switch to time based single password (TOTP) MFA (MSS-based Multi-Factor Authentication) and avoid using telephone numbers as password reset options to reduce this risk to high-risk accounts. At the end of Secureworks ‘ report, compromise indicators (IOCs), including the IP addresses used by this TrickBot variant as a vibrant webinjects proxy C2 server are accessible.
Functions and infection vectors regularly updated
TrickBot is one of, if not the most common of these days, malware, with upgrades to fresh variants found almost weekly by safety scientists. In July 2019, for example, the Trojan TrickBot added features to Windows Defender, got a fresh IcedID proxy module that robbed banking information and a distinct browser cookie stolen module. In January, scientists from CrowdStrike and FireEye discovered that other stakeholders use TrickBot to access earlier infected networks as an Access-as – a-Service. When a machine became a bot, the Trojan created reverse shells back at other actors, such as those at the back of Ryuk, to allow them to infiltrate the network further and drop payloads. One year previously, TrickBot had been updated by a screenlocker element on March 2018, which suggested its designers could begin keeping ransom victims as a backup if banking information exfiltration was not feasible. In July 2017, also, the banking Trojan was able to propagate itself by upgrading it to an automatic self-distribution element to increase the likelihood of infecting as many machines with little or no extra effort and compromises whole networks when and if possible. Credit: Bleeping computers