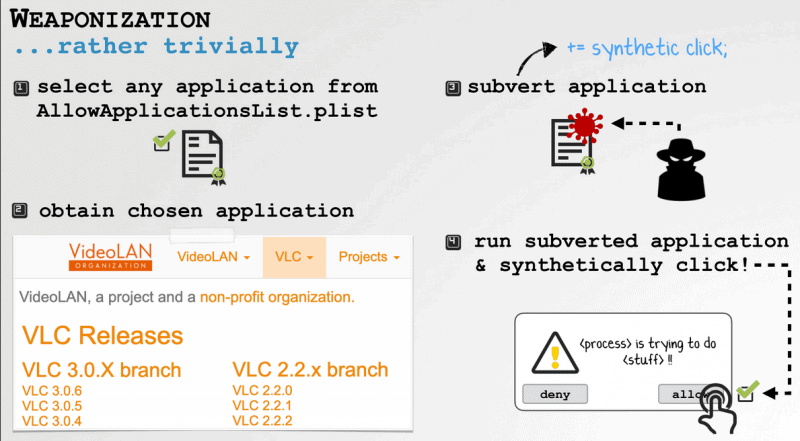
Last year he showed that the automation scripts in macOS High Sierra can be created synthetically, later in macOS Mojave privacy protection has been exported. He now found another way of bypassing security measures in order to perform Synthetic Clicks and access user data without the consent of the user. The vulnerability lies in the code of’ Apple,’ which only monitors the existence of the certificate but not the integrity of Trusted applications. An attacker may distort an application from the list of trusted apps to create synthetic clicks, which the operating system normally allows. You may use the following free web scanning tool to know the issue directly. Wardle showed the VLC Media Player attack to provide his malicious plugin to generate a synthetic click on prompt without the consent of the user.
“For VLC I just dropped into a new plugin, VLC loads it, and because my malicious plugin can generate a synthetic click, because the systems have a VLC, but do not validate the bundle so they are not tampered with,” he told Techcrunch. The attacker must have physical access to the Laptop to carry out the attack, but no higher privileges. Wardle reported Apple’s vulnerability a week ago, and the company confirms that the report is unclear but when it plans to address the vulnerability is not clear. — Objective-See (@objective_see) 2 June 2019