A more frequent strategy is to produce counterfeit and compelling websites that claim to be lawful software for attackers. However, these fake sites distribute Trojan password instead. For example, in the past we reported that websites were created that claim to be Windows system optimizers and VPN softwar, but that the AZORult Trojan actually infects the user. A fresh site, called gamebooster.pro, has been found by the Malware Hunter Team safety investigator, which is identical to the lawful pcgameboost.com website.
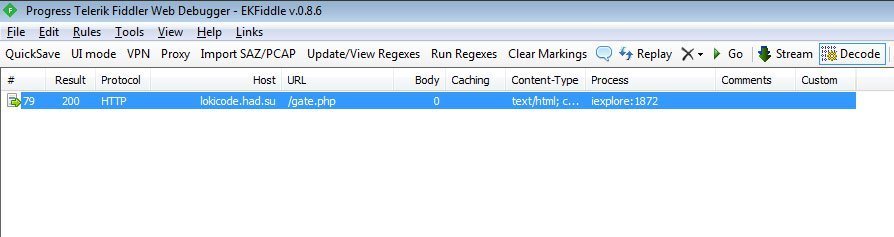
Fake Smart Game Booster Site The distinction, however, is that while pcgameboost.com distributes a lawful Smart Game Booster program, the gamebooster.pro site distributes the Baldr password and the Trojan data stealing. The Baldr Trojan is a fairly fresh malware sold for about $150 at underground hackers and criminal forums. While this sample includes strings identifying it as “Loki++ Stealer 2.0 Coded by Loki,” Vitali Kremez, Security Researcher, informed that this was a “Modified / Adjusted Baldr / Arkei Stealer.” Unlike other malware, Baldr has no persistence, so it only works once and then removes itself. However, if run, it tries to steal login credentials saved in the browser, browser profiles, cryptocurrency wallets, VPN client records, FTP programs, text documents, desktop files and telegram sessions. The Trojan also creates a screenshot of the active desktop when running. The data is then uploaded to the command and control server of the attackers where later it can be obtained. The information is uploaded to a server at lokicode.had.su. In this specific example.
Victim’s data being uploaded to attacker’s server Since the infection is only once performed, does not show an install screen and afterwards it deletes itself, victims would believe the program has a issue, because nothing is shown on the display. However, the attackers could now access their saved login credentials and other data and use them for a variety of attacks. It is therefore essential for users to research a site from which documents are downloaded beforehand. If the website has a strong reputation and is somehow linked with the program, it will probably be downloadable safely. However, if there is little or no data on a site, it should be prevented. Source: BleepingComputers