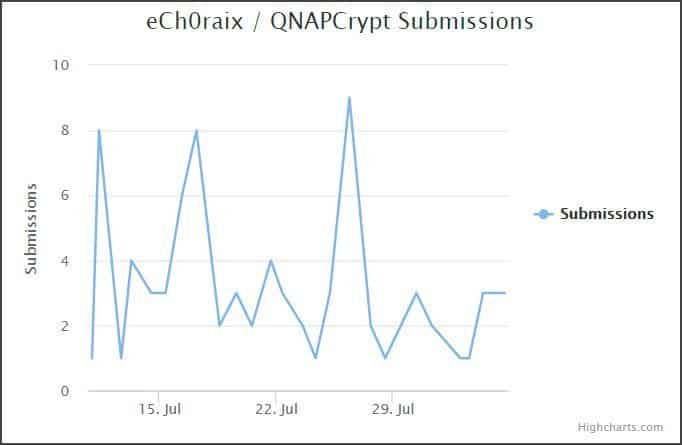
eCh0raix is a ransomware that since June 2018 has been targeting QNAP NAS devices by brutally forcing passwords and exploiting vulnerability to access the machine. Since the release, the submission chart by ID-Ransomware has shown a constant flow of fresh victims.
Once the ransomware accesses QNAP, it encrypts documents on the computer and requires bitcoins to decrypt documents. When encrypted, the.encrypted extension will be added to the names of the file. A ransom note called README.txt will also be developed.
Decoding eCh0raix / QNAPCryption Encrypted documents
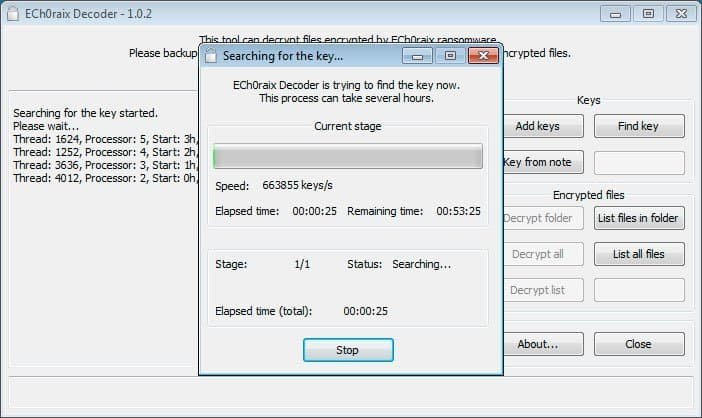
The excellent news was that BloodDolly, a safety scientist and ransomware specialist, published the eCh0raix Decoder for this ransomware in our support subject. This decoder allows victims to brute the decryption key into encrypted files and use it to restore their files. Nevertheless, the present decrypter version supports only victims who were infected before 17 July. BloodDolly works to fix it for newer variants. A fast way to say if the fresh unbreakable version has 173 characters at the end of the ransom note. Download ECh0raixDecoder.exe from the link below to get began. After downloading, you can remove the documents and read the README.txt included to know how to use the program. The quickest way to brutalize the key is to have an encrypted unencrypted file pair and to use it to discover the key. Typically, this can be done using pictures in the folder C:\Users\Public\Pictures\Sample Pictures. If that is not possible, the decryptor can be used to brute your password from any encrypted file, but it may take several hours to complete this procedure.
Once you have discovered a key, you can add it to the decrypter and decrypt the documents on your desktop. You can ask questions on the eCh0raix Ransomware-QNAPCrypt Support Topic for customers who need assistance with decrypter.