Worsening matters, the ransomware has been backed by a solid distribution campaign and has been making regular victims for the past two months on a daily basis.
FIRST DEATHRANSOM VERSIONS DIDN’T ENCRYPT ANYTHING
In November 2019, First DeathRansom was announced. Early variants of this malware have been considered a joke. DeathRansom at the time simply imitated being a ransomware without encrypting any of the data of a victim. These first iterations will apply a file extension to all the files of a consumer and drop a ransom note on the user’s asking for money device. All this was done in an attempt to deceive a target into accepting a demand for a ransom, without the customer knowing that their data had not been secured. As stated at the time, deleting the second extension from any file was all a person had to do to regain access to their encrypted files.
NEW VERSION RELEASED WITH A SOLID ENCRYPTION SCHEME
Though, development has progressed on the DeathRansom application, and new versions are now operating as true ransomware. According to Fortinet, the new DeathRansom strains use a complex combination of “Curve25519 algorithm for the Elliptic Curve Diffie-Hellman (ECDH) key exchange scheme, Salsa20, RSA-2048, AES-256 ECB, and a simple block XOR algorithm for encrypting files.”[ see picture above] While security researchers are still looking at DeathRansom’s implementation faults encryption scheme, the ransomware appears to be a failure.
FORTINET TRACKS DOWN THE DEATHRANSOM AUTHOR
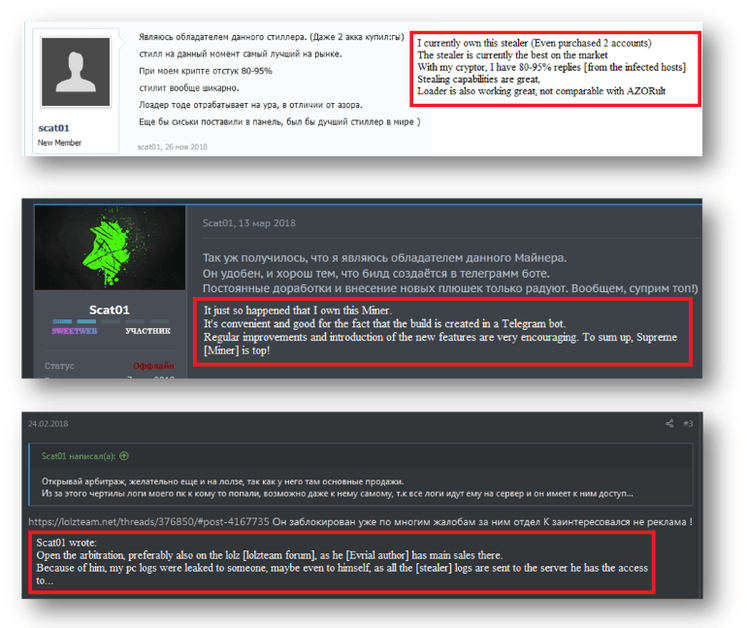
But the investigation into DeathRansom by Fortinet was not limited to the analysis of the source code of this new malware. Scientists have looked for information about the developer of the ransomware. The Fortinet team was able to successfully connect the DeathRansom ransomware to a malware developer responsible for a wide range of cybercrime operations going back years by removing strings from the DeathRansom source code and websites spreading the ransomware payloads. Fortinet said this malware developer had been infecting users with numerous password stealers (Vidar, Azorult, Evrial, 1ms0rryStealer) and cryptocurrency miners (SupremeMiner) before creating and distributing DeathRansom. According to various Fortinet ads found on underground hacking forums, the DeathRansom author seems to have spent years infecting users with malware, extracting usernames and passwords from their browsers, and selling the stolen credentials online. Such previous efforts for ransomware left a large trail of hints that were gathered by Fortinet researchers. These included the nicknames scat01 and SoftEgorka, the email addressvitasa01[@]yandex.ru, a Russian phone number, and the domain gameshack[.]ru (which seems to have been owned and operated by the DeathRansom author rather than a compromised site). Using these metrics, Iandex. Market, Twitter, Whatsapp, Instagram, Instragram, and Facebook profiles were discovered by researchers. All of these were linked back to a young Russian named Egor Nedugov who lived in a small Russian town near Rostov-on-Don, Aksay. Past posts on hacker forums show that Nedugov, working under the Scat01 pseudonym, posted reports of the malware strains he used at the time, and that Fortinet subsequently monitored and reported in their study, such as Vidar, Evrial, and SupremeMiner.
Image: Fortinet Fortinet mentions all of Nedugov’s online accounts and the apparent network of links between them in a detailed two–series report released today. Fortinet claimed they found the right guy behind DeathRansom and discovered even more online profiles from the same actor they didn’t include in their study. In fact, the DeathRansom author even seems to have violated one of the underground cybercrime scene’s unwritten rules by “phishing and scamming his forum friends.” “That’s why almost all of his profiles on underground forums have finally been blocked,” Fortinet stated. DeathRansom is currently being spread through email campaigns for phishing. The Fortinet report contains vulnerability markers that organizations should integrate into their security products to prevent infection of business networks. Fortinet also said it is currently focusing on evaluating the foor of potential flaws in the ransomware encryption process, which they expect will be used to create a free decrypter to assist former victims.