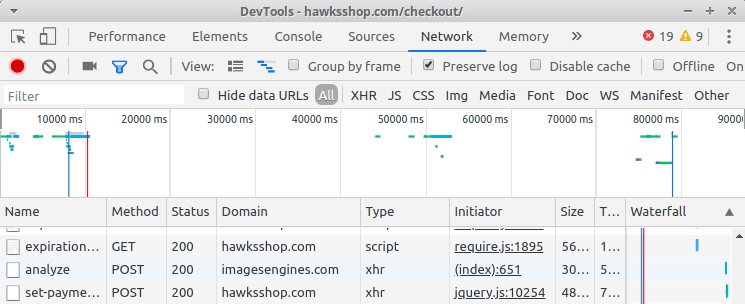
This attack is known as MageCart infection and occurs when an attacker compromises an ecommerce site to add JavaScript to the checkout or cart pages. Then this script robs the credit card and address data entered in these pages and sends it to a remote server to collect from the attackers. Sanguine Security reports that a MageCart script was detected on the checkout page for the Atlanta Hawks ‘ online shop on 20 April, as shown below.
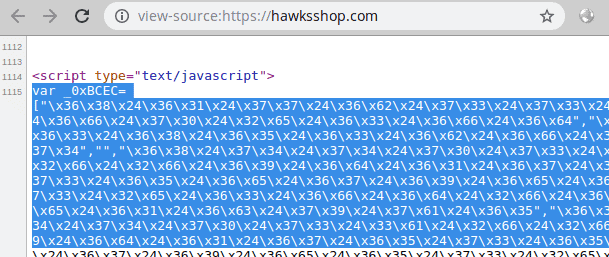
Script injected into hawksshop.com This script has been obscured when injected into the page, but you can see certain areas related to the credit cards collected by the script if they are deconfused by the researchers.
Strings in unfuscated script When an user purchased something while the site was infected, they would request an additional image engine[.]com from the remote website, which is controlled by the attacker. This request can be viewed by image motors[.]com in the network traffic under Sanguine Security.
Connect to the Remote Site The attackers would just have to log on to their server to view what has been collected to get the stolen payment information. According to a tweet by Willem de Groot from Sanguine, the site was no longer affected by the script. At the time of the statement Groot continued to see the script. It seems that the Hawks have now started cleaning up their site because it is now for a long time to maintain.
Hawks Store under maintenance It is strongly suggested to those who recently purchased something from Hawksshop.com, that you report this incident to your credit card company and monitor your fraudulent activity statement. Unfortunately, there is no solution to protecting sites against these types of attacks on how to protect them against MageCart attacks. The best solution is to ensure that you have control over any third-party scripts that you use, update your web platform and monitor new vulnerabilities found in plugins.