The research team, consisting of Purdue University’s Hui Peng and Swiss Federal Institute of Technology Lausanne’s Mathias Payer, said all the bugs were found using a new tool they developed, called USBFuzz. The tool is what security practitioners call a fuzzer. Fuzzers are applications that allow security researchers to submit large quantities of null, unwanted, or random data into other programs as inputs. Security researchers then analyze how the software being tested conducts the discovery of new bugs, some of which may be maliciously exploited.
A New Portable USB Fuzzer Built by Academics
Peng and Payer created USBFuzz to test USB drivers, a new fuzzer designed specifically for testing the USB driver stack of modern-day operating systems. “USBFuzz uses a software-emulated USB device at its heart to provide drivers with random device data (when they conduct IO operations),” the investigators said. “As the emulated USB interface works at system level, it is straightforward to port it to other platforms.” This enabled the research team not only to test USBFuzz on Linux, where most fuzzer programs work, but other operating systems too. Researchers have said USBFuzz was checked on:
9 recent versions of the Linux kernel: v4.14.81, v4.15,v4.16, v4.17, v4.18.19, v4.19, v4.19.1, v4.19.2, and v4.20-rc2 (the latest version at the time of evaluation) FreeBSD 12 (the latest release) MacOS 10.15 Catalina (the latest release) Windows (both version 8 and 10, with most recent security updates installed)
Study Team Finds 26 New Bugs
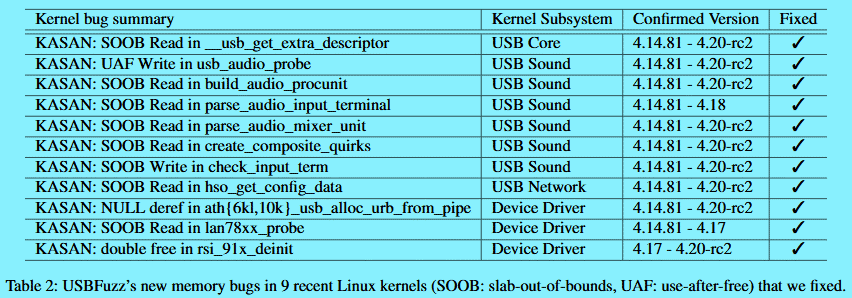
After their experiments the research team said they found a total of 26 new bugs with the help of USBFuzz. Researchers found one bug in FreeBSD, three in MacOS (two resulting in an unplanned reset and one freezing of the system), and four in Windows 8 and 10 (resulting in Death’s Blue Screens). But the vast majority, and the most serious, of bugs were found in Linux — 18 in all. Sixteen were high-security impact memory bugs in different Linux subsystems (USB core, USB sound, and network), one bug resided in the Linux USB host controller driver, and the last one was in a USB camera driver. Peng and Payer said they reported these bugs to the Linux kernel team and suggested patches to reduce “the burden on the kernel developers while addressing the identified vulnerabilities.” Of the 18 Linux bugs, 11 have received a patch since their initial reports last year, the research team said. Ten of those 11 bugs were also given a CVE, a special code assigned to major security vulnerabilities.
Further updates for the remaining seven problems are also expected in the immediate future. “The remaining bugs fall into two classes: those still being published under embargo and those discovered and documented simultaneously by other researchers,” said the researchers.
USBFuzz is Open Source
Yesterday Payer released a draft of a white paper from the research team detailing their work on USBFuzz. Peng and Payer are planning to present their research at the Virtual Security Conference at Usenix Security Symposium, scheduled for August 2020. Similar work has been done in the past. In November 2017, a security engineer from Google used a Google-made fuzzer called syzkaller to discover 79 bugs affecting USB drivers on the Linux kernel. Peng and Payer said that USBFuzz is superior to previous tools like vUSBf, syzkaller, and usb-fuzzer because their tool gives testers more control over the test data and is also portable across operating systems, contrary to all of the above, which usually only work on * NIX systems. Following Peng and Payer’s Usenix talk USBFuzz is expected to be published on GitHub as an open source project. The repo can be found here. Copies of Peng and Payer ‘s paper, entitled “USBFuzz: A System for Computer Emulation Usb Drivers Fuzzing,” are available here and here in PDF format.